OAuth2 Authorization Code Grant
In the authorization code flow a user authorizes with the authorization server. After that an authorization code is issued. This authorization code is then exchanged for an access token. The access token can then be used to access a resource.
OpenID Connect can be used supplementary to the OAuth2 authorization code flow. It appends, among other duties, an id token to the access token request and follows with the userinfo step after the reception of the access token. The id token is used for authentication. In the userinfo step the access token is used to gather information about the user for further processing.
This flow is suitable in situations where the resource owner wants to interact with the resource through a user agent and has the ability to manually log in. The client also needs to be able to interact with the user agent, e.g. for redirecting.
Securing your Resources with OAuth2 using Membrane
Membrane Service Proxy can be used to authorize HTTP requests based on the RFC 6749 OAuth 2.0 Authorization Framework, OpenID Connect Core and OpenID Connect Discovery . It supports the OAuth2 / OpenID Connect authorization code flow.
Membrane Service Proxy can act as the authorization server and client of the OAuth 2.0/OpenID-Connect authorization flow. Both ( authorization server and client ) can be run in one or seperate Membrane Service Proxy instances. Of course either the authorization server or the client can be replaced by other software conforming to the OAuth 2.0 Authorization Framework, OpenID Connect Core and OpenID Connect Discovery standards ( OpenID providers ).
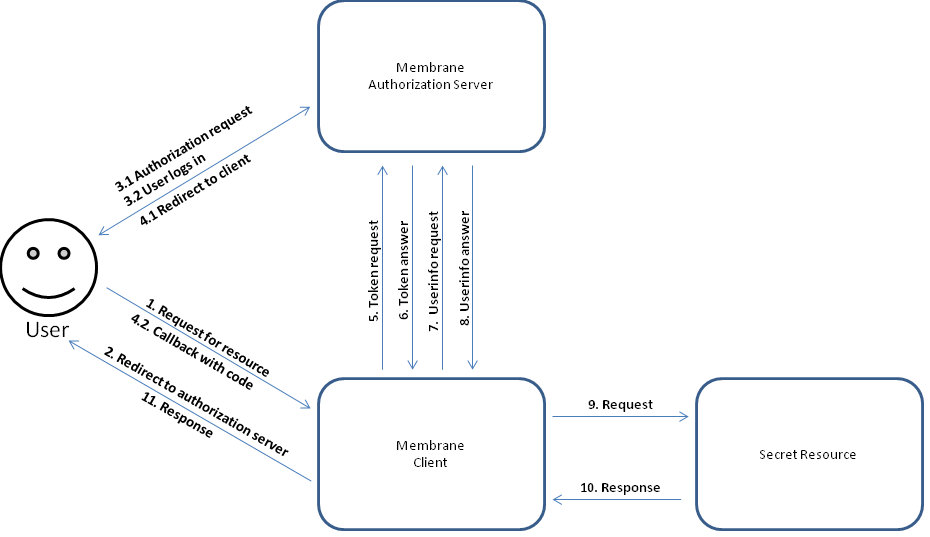
Figure1:
The flow comprises the steps:
1. The user starts the authorization process by requesting access to the secret resource. 2. The client redirects the user to the authorization server to start the login procedure. 3.1 The user automatically calls the authorization endpoint ( through the redirect of the client ). 3. 2 The user authorizes with his/her credentials and accepts the information on the consent page. 4. After successful authorization the user is redirected to the client and the clients callback url is called with, among other parameters, the access code. 5. The client requests an access token in exchange for the access code. 6. The authorization server answers with an access token and optionally an id token. 7. The client requests userinfos with his access token. 8. The authorization server answers with the information about the user. 9. The client collects all OAuth2 / OpenID Connect data ( which can then be further prepared for the secret resource e.g. with a Groovy interceptor ) and starts retrieving the secret resource. 10. + 11. The resource is delivered to the user.
Getting Started
See $MEMBRANE_HOME/examples/oauth2/membrane in the Membrane Service Proxy distribution for a working example.