SSL/TLS Termination and Tunneling
Membrane ESB supports SSL in various setups:
How to configure SSL for Membrane is described in the SSL reference.
SSL for unsecured Servers
A client can establish an encrypted SSL connection to the Membrane Router. The router terminates the SSL channel and communicates in plain HTTP or SOAP with the server. Using this configuration you can provide SSL encryption and authentication even if your service does not provide SSL. The Membrane Router can also do loadbalancing or access control.
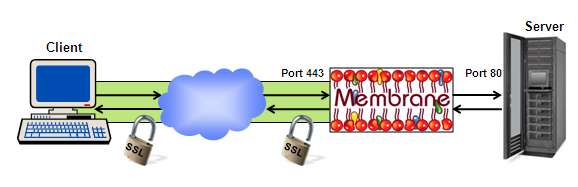
Figure1:
See also the example/ssl-server directory of the Membrane distribution for example configuration files for this scenario.
SSL Tunnel to the Server
Membrane Router can enable clients that do not support SSL to communicate with a SSL secured server. To secure the connection the traffic is encrypted by the router before it enters the unsecured network.
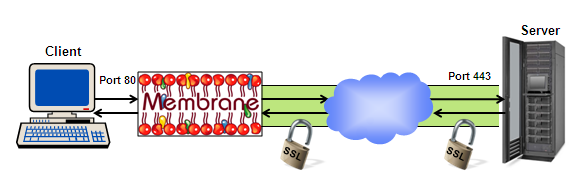
Figure2:
See also the example/ssl-client directory of the Membrane distribution for example configuration files for this scenario.
Monitoring a SSL Connection
Because a SSL connection is encrypted it is not possible to monitor the traffic between the client and the server. By using two SSL connections, one between client and monitor and one between monitor and server, it is possible to analyze and monitor the traffic. So both client and server think they are communicating point to point securely with their peer.
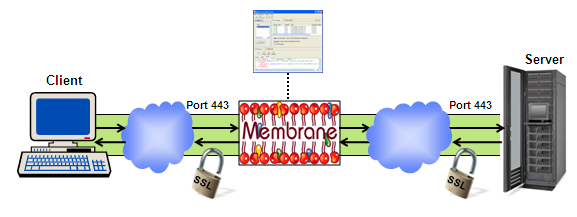
Figure3:
SSL Tunnel and VPN
A SSL tunnel can route traffic between an unsecured client and an unsecured server over the hostile internet. At each organisation a Membrane Router can work as SSL termination point and provide the desired encryption and authentication.
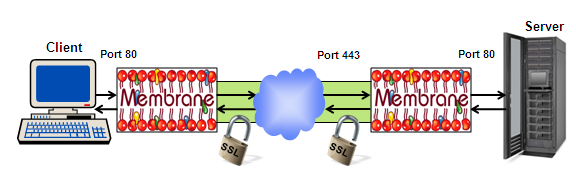
Figure4:
Technical Configuration
Inbound and outbound SSL can be configured using the ssl element in proxies.xml.